
The ECDH key establishment process. The ECDH key establishment process. | Download Scientific Diagram
GitHub - shesek/ecdh-es: Elliptic Curve Diffie-Hellman with ephemeral-static keys implementation for NodeJS

Elliptic Curve Diffie-Hellman (ECDH) Key Exchange Protocol. Two users,... | Download Scientific Diagram
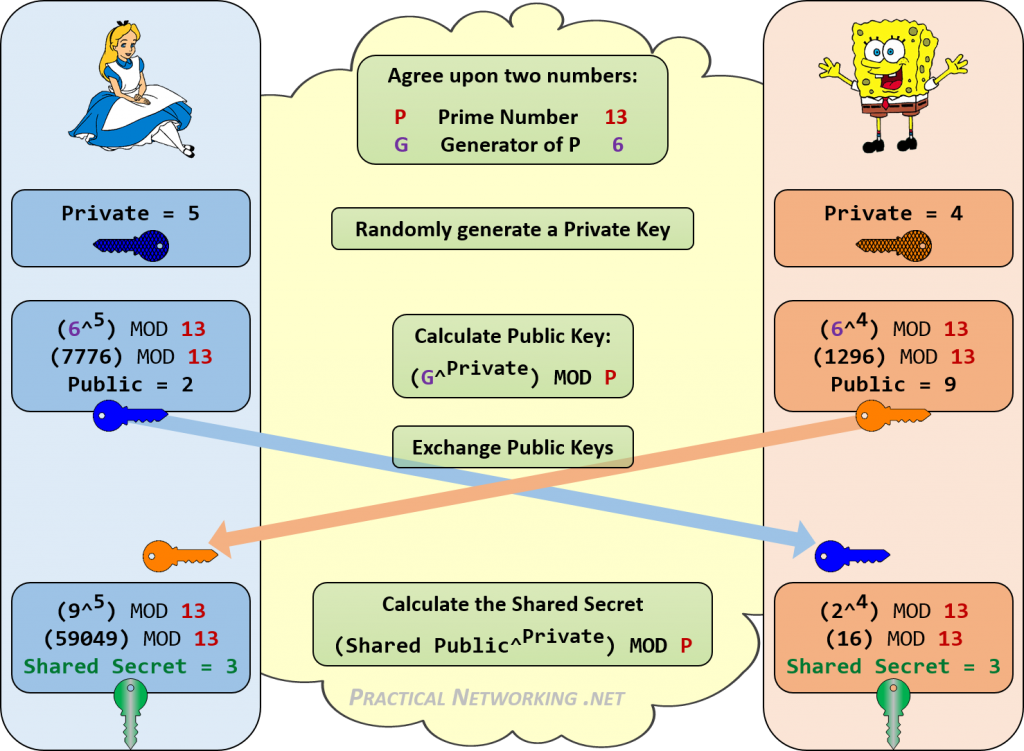
Implementing Elliptic-curve Diffie–Hellman Key Exchange Algorithm using C# (cross-platform) | David Tavarez

6: DS2432 Authenticated ECDH unified authentication and key exchange... | Download Scientific Diagram
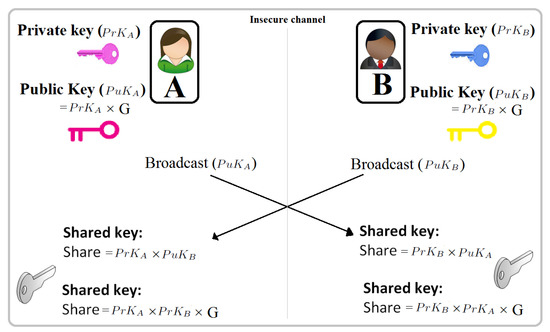


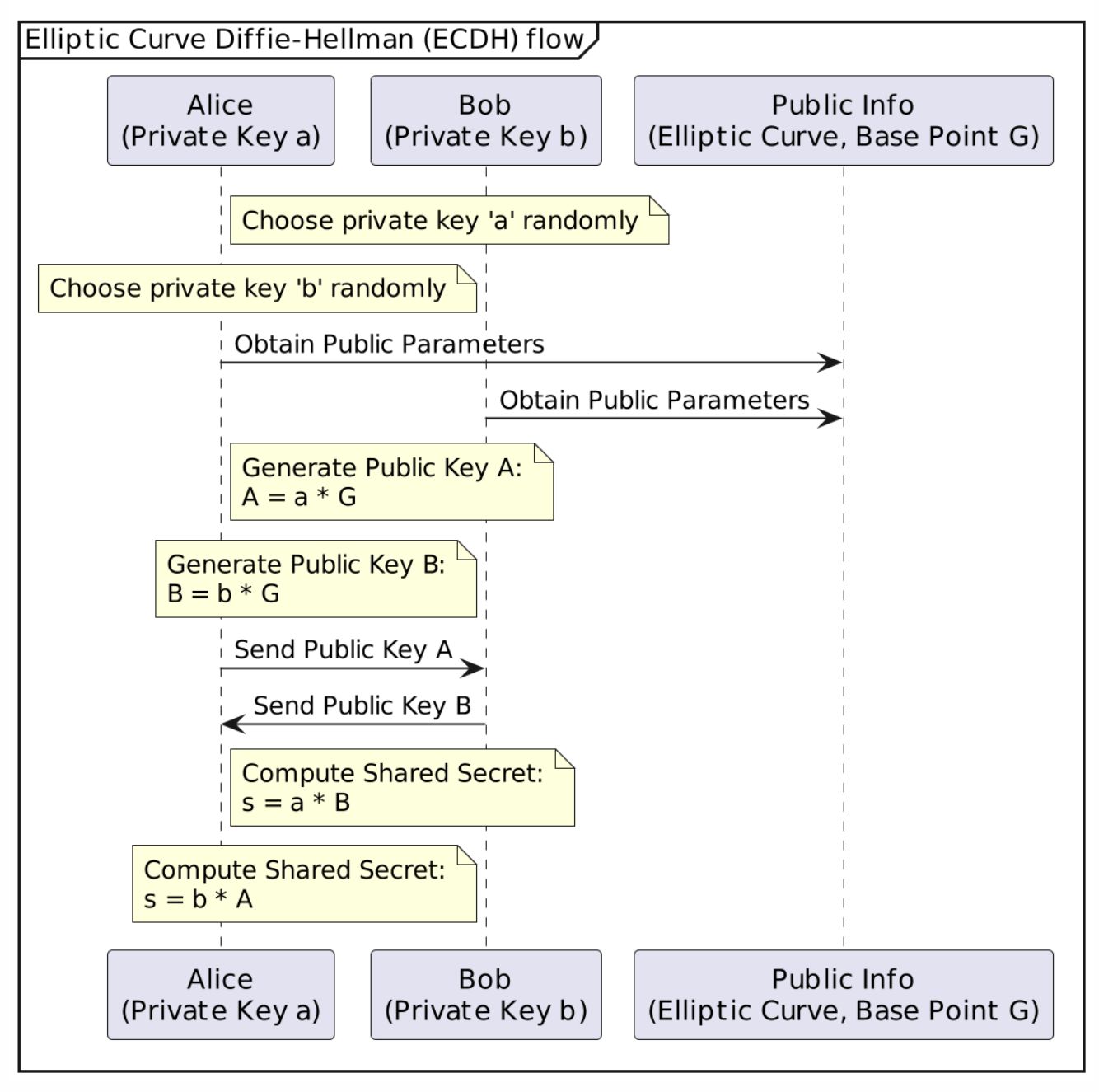



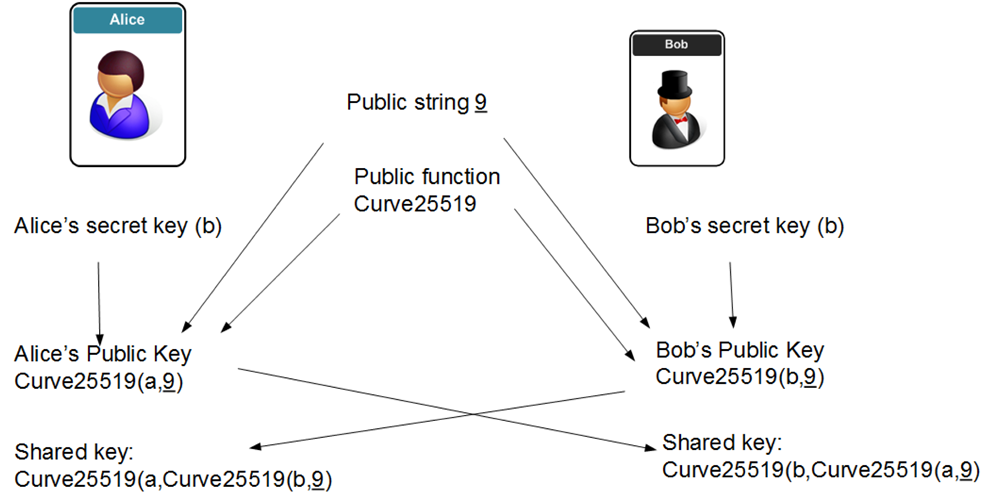


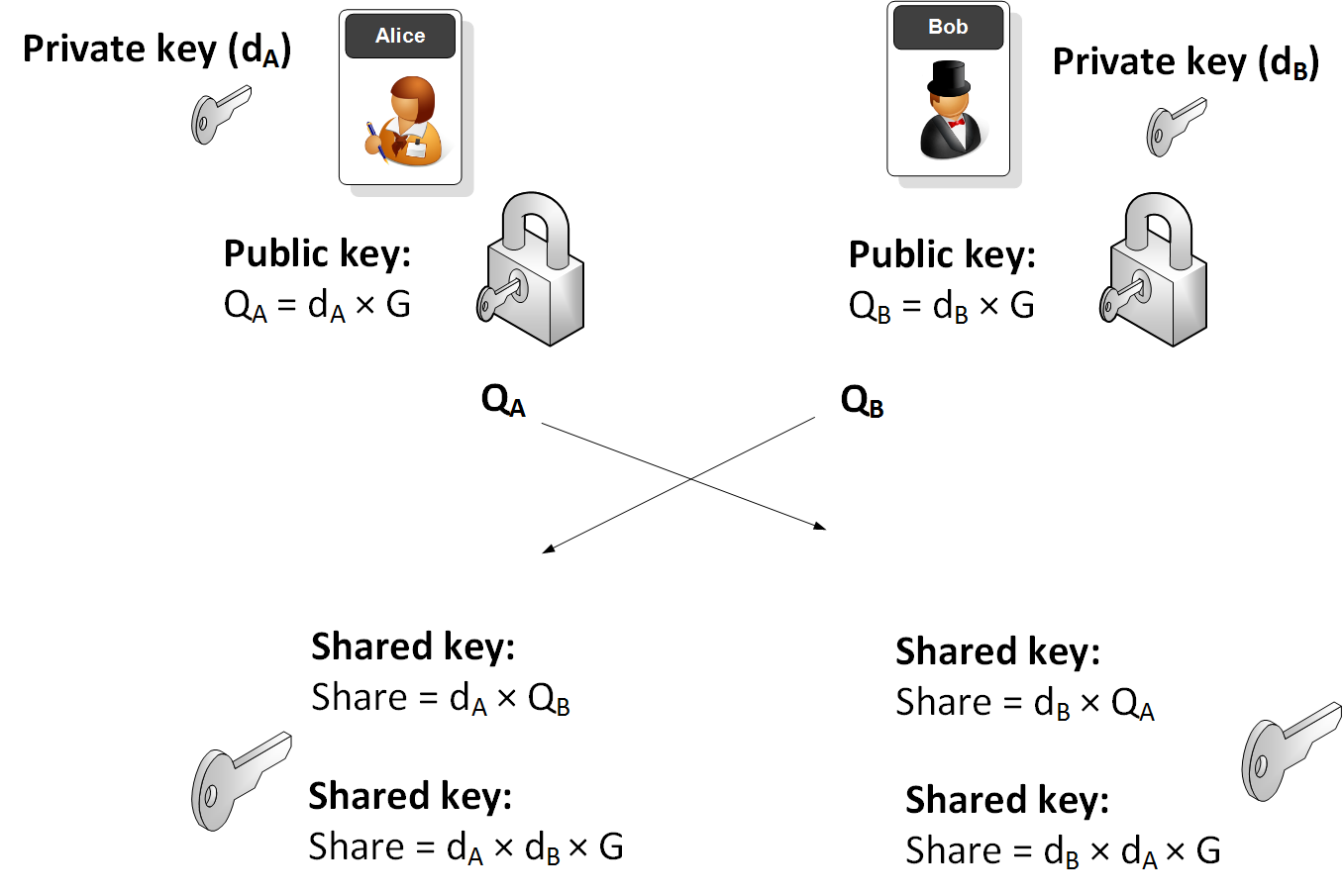
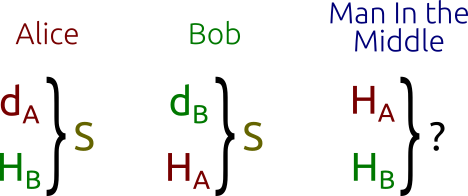

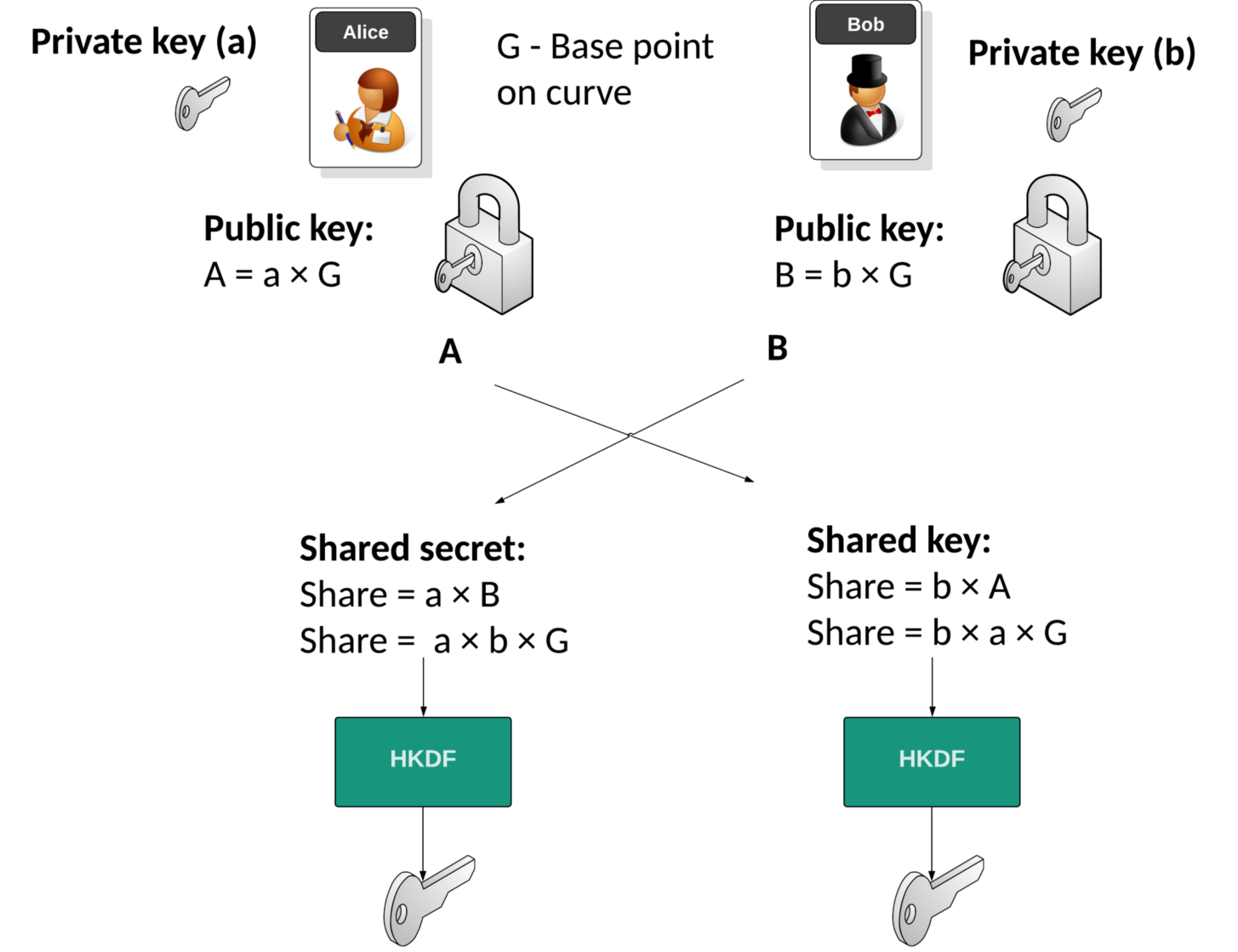


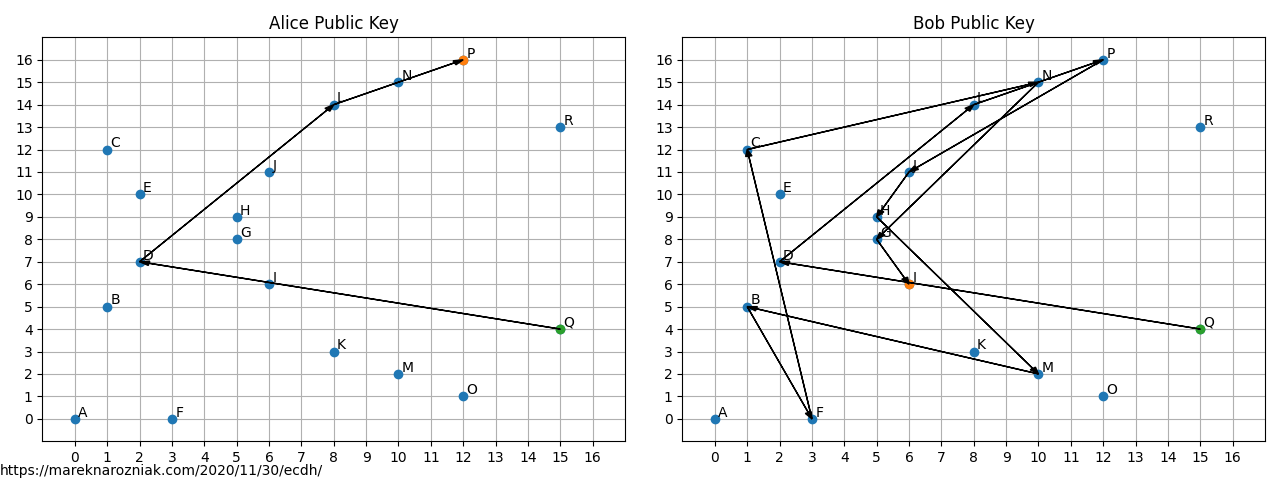

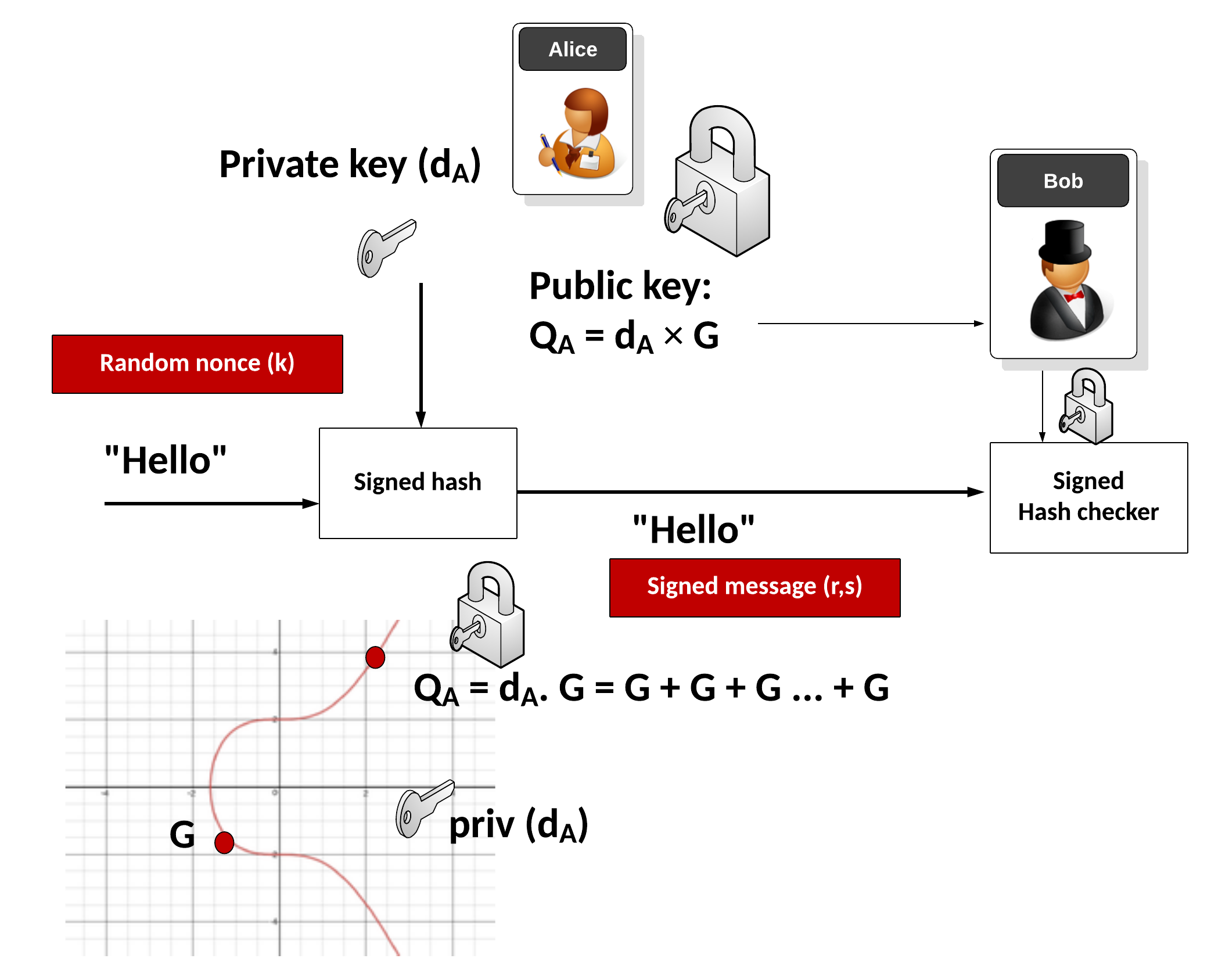
![PDF] The Elliptic Curve Diffie-Hellman (ECDH) | Semantic Scholar PDF] The Elliptic Curve Diffie-Hellman (ECDH) | Semantic Scholar](https://d3i71xaburhd42.cloudfront.net/de032e79b6116aeb3efc26de258903d6fdc24a08/1-Figure1-1.png)
